data protection
data security
+ 2 more ...
Secure Solutions at Lizard Global: How We Protect Your Data
05 Nov 2020
by Lotte, Digital Content Specialist
05 Nov 2020
by Lotte, Digital Content Specialist
data protection
data security
cybersecurity
encryption
Secure Solutions at Lizard Global: How We Protect Your Data
Table of contents
Contact us
We will get back to you in the next 48 hours.

At Lizard Global, the security of your data is our number one priority. That’s why our developers are specialized in protecting your data in any state, at any moment.
Follow Lizard Global on Facebook, Instagram, and LinkedIn.
At Lizard Global, we believe that the security of your data should be the number one priority at all times. Our development team is always up-to-date with the latest technologies and innovations in the field of data protection, and we develop our applications following the principles of security by default and privacy by design. This means that all our applications, no matter what type or function, are built with security and privacy in mind. We make sure your software is heavily protected and only uses the data it requires in order to function properly, nothing more. How do we do that? Keep on reading to find out how we develop secure solutions for your business.
At Lizard Global, we focus on three key aspects when developing a secure application:
- Confidentiality: only those with access rights can view privileged content, such as user data.
- Integrity: only users with authorization can access or amend the system’s content
- Availability: information will always be available to authorized users of the system
These three key aspects are under our continuous care and maintenance, and make sure that the content within our applications is always accessible for the people with the authorization to access it, and can’t be accessed or tampered with by people without permission. This way, you and your end-users can be sure of the fact that no one, except for those with authorization, can access the personal information that’s stored in the app.
Our Security Design Principles
Our specialized technical team at Lizard Global knows everything about the implementation of secure digital solutions, following our trusted security design principles. Because every single one of our digital solutions is unique, we identify key security design principles that are perfectly aligned with the software we develop. In order to understand how we do that, let’s have a look at our security design principles:
Security by default
For every single application we develop, we make sure that no one has access to data “by default”. We evaluate the security risks of all our digital solutions, and make sure that access is only allowed when absolutely necessary. We prioritize the safety of your user data by making sure that our code is built in such a way it requires a minimal amount of access to user data in order to function properly.
Password policies
Picking a safe password for your application can be difficult, and at Lizard Global we don’t rely on our users to keep their data safe. Instead, we take the responsibility to make our systems secure through strict password policies. These policies stimulate our users to register strong and safe passwords, as well as restricting them from reusing the same username as a password, or using the same password more than once.
Role-based access control
Depending on the requirements of your business, our digital solutions are built in such a way that they are used by different users with different roles, responsibilities, and authority levels. Our technical experts are experienced with incorporating role-based access control in the frontend and backend of your application. All user actions are continuously checked through a role-permission matrix before granting them access to view or amend data. This way, the right person can access the right data without any risk.

In-depth defense
Every application is different, and depending on the level of sensitivity of the data inside your application, we can incorporate multi-factor authentication (MFA) systems. An MFA requires users to go through more than one authentication level. Besides simply requesting users to enter a username and password, our MFA implementations provide a robust authentication process by sending a time-based security code via SMS, email, or an official authenticator such as Google Authenticator or Authy.
Economy of mechanisms
Our software is built on a microservice architecture. This means that each service or functionality is a simple and small module, contained on its own and programmed to execute a task. Separating these modules prevents the entire system from being at risk in case of a security breach, as we can immediately disconnect all services.
Minimal attack surface area
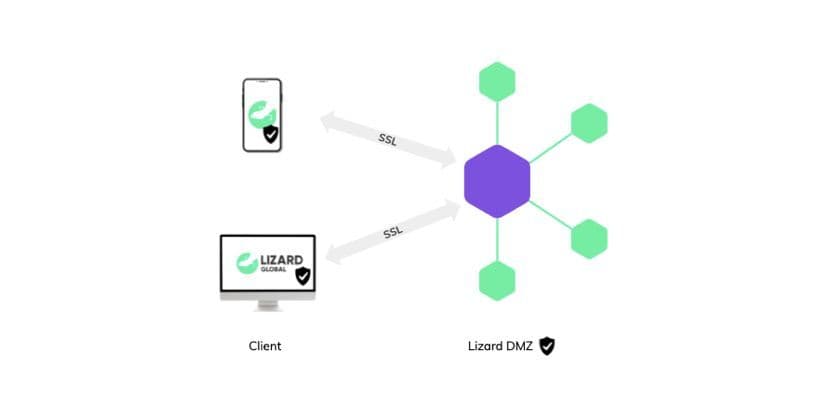
In order to make our applications as safe and secure as possible, we make sure to minimize the potential points of attack. All our services are made available via an API gateway that exposes the external-facing services only to authenticated user-requests. The API only allows access from users they can identify and authenticate, which greatly decreases the chance of security breaches. API authentication creates a so-called demilitarized zone (DMZ), which adds an extra layer of security by limiting access to sensitive information.
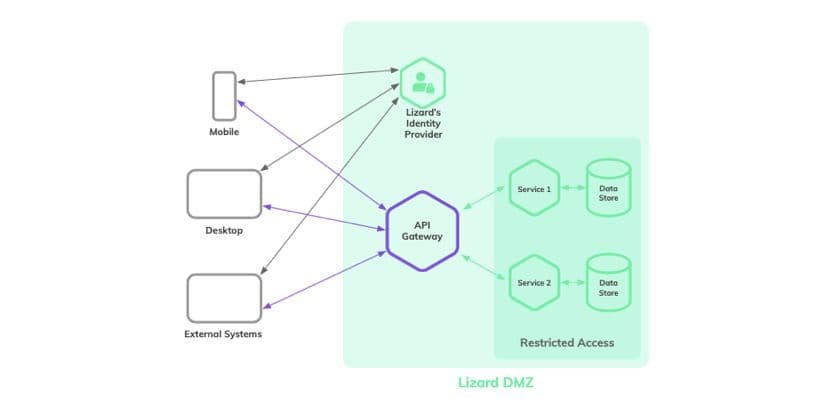
The separated modules within the microservice architecture each carry out a specific task. In case users want to access these services, they need to go through an API Gateway which only gives access to people with an authentication token, or authToken. If requests for access don’t consist of a valid authToken, access will be denied.
Identity Provider
Lizard’s Identify Provider is a separate server that is configured with end-to-end security, handling only authentication. The credentials of a user are passed to the server, which then authenticates and generates an authentication token. This authToken is like a passport, which allows access to the DMZ data. The Lizard’s Identity Provider is the only server that will receive the user credentials. This is an additional security measure we take to protect user credentials.
Backup data
Every single one of the applications built at Lizard Global incorporates scheduled backups. In the case of a security breach, our backups are able to restore any data and ensure the protection of sensitive information.

Three states of data security
The organization of your business’ data appears in three different states: data in use, data in motion, and data at rest. While data in motion can be the most vulnerable state regarding security threats, our processes and systems ensure the safety of your data during each state.
Data at rest
Data at rest can be described as information that’s not in use and stored somewhere on a server. Because this data is not in motion, it’s easier to safely lock away, and is therefore relatively secure. Often, data at rest is primarily protected by firewalls and/or strict security rules. If the stored information is particularly sensitive or private, the data is protected by encryption, which adds an additional layer of defense in the rare case of a security breach. For data at rest that require high-level security, we incorporate audit logs to track and report information about interactions with the stored data, such as views or amends.
Data in use
Data in use is information that’s being processed, accessed, read, or amended. We protect data in use by making sure this information can only be accessed by authenticated and authorized users with an API authentication key. Our systems proactively improve the security of data in use by implementing strict security rules to disable user accounts with suspicious activities, such as multiple unsuccessful login attempts. Depending on the sensitivity of your data, we also provide users with the implementation of a role-based security system, to not only restrict access to certain data collections, but also restrict the access to certain branches of their data collections.
Data in motion
Data in motion is probably the most sensitive for security breaches, as it travels from one place to another, which requires a safety measure that travels along. The most used and trusted way to secure data in motion is by ensuring these transmissions are encrypted. Data encryption makes sure that data in motion is being turned into encoded combinations of characters, while providing the sender and receiver with a personal key to turn these signs back into the original data. When your data is going from point A (a server) to point B (a client), we encrypt the contents, so that anyone who gains access to it won’t be able to make sense of it. Only point B has the so-called decryption key to turn the data back into its original form and view the contents. At Lizard Global, we always incorporate a Security Service Layer (SSL) to our communication channels, as an effective way to safeguard your data in motion.
Need a hand?
Every digital solution is unique, and our experienced team at Lizard Global has the right skill-set to build a fully secure solution, based on the unique requirements of your business and software solution. At Lizard Global, the safety of your data is our number one priority, which is why we consider the vulnerabilities of your data from all angles: data at rest, data in use, and data in motion. This way, your data is safe at all times.
Do you want to know more about our secure solutions at Lizard Global? Or do you have questions about our security systems you’d like to ask our experts? Get in touch with us, and we gladly tell you all you need to know about the protection of your personal data.


At Lizard Global, the security of your data is our number one priority. That’s why our developers are specialized in protecting your data in any state, at any moment.
Follow Lizard Global on Facebook, Instagram, and LinkedIn.
At Lizard Global, we believe that the security of your data should be the number one priority at all times. Our development team is always up-to-date with the latest technologies and innovations in the field of data protection, and we develop our applications following the principles of security by default and privacy by design. This means that all our applications, no matter what type or function, are built with security and privacy in mind. We make sure your software is heavily protected and only uses the data it requires in order to function properly, nothing more. How do we do that? Keep on reading to find out how we develop secure solutions for your business.
At Lizard Global, we focus on three key aspects when developing a secure application:
- Confidentiality: only those with access rights can view privileged content, such as user data.
- Integrity: only users with authorization can access or amend the system’s content
- Availability: information will always be available to authorized users of the system
These three key aspects are under our continuous care and maintenance, and make sure that the content within our applications is always accessible for the people with the authorization to access it, and can’t be accessed or tampered with by people without permission. This way, you and your end-users can be sure of the fact that no one, except for those with authorization, can access the personal information that’s stored in the app.
Our Security Design Principles
Our specialized technical team at Lizard Global knows everything about the implementation of secure digital solutions, following our trusted security design principles. Because every single one of our digital solutions is unique, we identify key security design principles that are perfectly aligned with the software we develop. In order to understand how we do that, let’s have a look at our security design principles:
Security by default
For every single application we develop, we make sure that no one has access to data “by default”. We evaluate the security risks of all our digital solutions, and make sure that access is only allowed when absolutely necessary. We prioritize the safety of your user data by making sure that our code is built in such a way it requires a minimal amount of access to user data in order to function properly.
Password policies
Picking a safe password for your application can be difficult, and at Lizard Global we don’t rely on our users to keep their data safe. Instead, we take the responsibility to make our systems secure through strict password policies. These policies stimulate our users to register strong and safe passwords, as well as restricting them from reusing the same username as a password, or using the same password more than once.
Role-based access control
Depending on the requirements of your business, our digital solutions are built in such a way that they are used by different users with different roles, responsibilities, and authority levels. Our technical experts are experienced with incorporating role-based access control in the frontend and backend of your application. All user actions are continuously checked through a role-permission matrix before granting them access to view or amend data. This way, the right person can access the right data without any risk.

In-depth defense
Every application is different, and depending on the level of sensitivity of the data inside your application, we can incorporate multi-factor authentication (MFA) systems. An MFA requires users to go through more than one authentication level. Besides simply requesting users to enter a username and password, our MFA implementations provide a robust authentication process by sending a time-based security code via SMS, email, or an official authenticator such as Google Authenticator or Authy.
Economy of mechanisms
Our software is built on a microservice architecture. This means that each service or functionality is a simple and small module, contained on its own and programmed to execute a task. Separating these modules prevents the entire system from being at risk in case of a security breach, as we can immediately disconnect all services.
Minimal attack surface area
In order to make our applications as safe and secure as possible, we make sure to minimize the potential points of attack. All our services are made available via an API gateway that exposes the external-facing services only to authenticated user-requests. The API only allows access from users they can identify and authenticate, which greatly decreases the chance of security breaches. API authentication creates a so-called demilitarized zone (DMZ), which adds an extra layer of security by limiting access to sensitive information.

The separated modules within the microservice architecture each carry out a specific task. In case users want to access these services, they need to go through an API Gateway which only gives access to people with an authentication token, or authToken. If requests for access don’t consist of a valid authToken, access will be denied.
Identity Provider
Lizard’s Identify Provider is a separate server that is configured with end-to-end security, handling only authentication. The credentials of a user are passed to the server, which then authenticates and generates an authentication token. This authToken is like a passport, which allows access to the DMZ data. The Lizard’s Identity Provider is the only server that will receive the user credentials. This is an additional security measure we take to protect user credentials.
Backup data
Every single one of the applications built at Lizard Global incorporates scheduled backups. In the case of a security breach, our backups are able to restore any data and ensure the protection of sensitive information.

Three states of data security
The organization of your business’ data appears in three different states: data in use, data in motion, and data at rest. While data in motion can be the most vulnerable state regarding security threats, our processes and systems ensure the safety of your data during each state.
Data at rest
Data at rest can be described as information that’s not in use and stored somewhere on a server. Because this data is not in motion, it’s easier to safely lock away, and is therefore relatively secure. Often, data at rest is primarily protected by firewalls and/or strict security rules. If the stored information is particularly sensitive or private, the data is protected by encryption, which adds an additional layer of defense in the rare case of a security breach. For data at rest that require high-level security, we incorporate audit logs to track and report information about interactions with the stored data, such as views or amends.
Data in use
Data in use is information that’s being processed, accessed, read, or amended. We protect data in use by making sure this information can only be accessed by authenticated and authorized users with an API authentication key. Our systems proactively improve the security of data in use by implementing strict security rules to disable user accounts with suspicious activities, such as multiple unsuccessful login attempts. Depending on the sensitivity of your data, we also provide users with the implementation of a role-based security system, to not only restrict access to certain data collections, but also restrict the access to certain branches of their data collections.
Data in motion
Data in motion is probably the most sensitive for security breaches, as it travels from one place to another, which requires a safety measure that travels along. The most used and trusted way to secure data in motion is by ensuring these transmissions are encrypted. Data encryption makes sure that data in motion is being turned into encoded combinations of characters, while providing the sender and receiver with a personal key to turn these signs back into the original data. When your data is going from point A (a server) to point B (a client), we encrypt the contents, so that anyone who gains access to it won’t be able to make sense of it. Only point B has the so-called decryption key to turn the data back into its original form and view the contents. At Lizard Global, we always incorporate a Security Service Layer (SSL) to our communication channels, as an effective way to safeguard your data in motion.

Need a hand?
Every digital solution is unique, and our experienced team at Lizard Global has the right skill-set to build a fully secure solution, based on the unique requirements of your business and software solution. At Lizard Global, the safety of your data is our number one priority, which is why we consider the vulnerabilities of your data from all angles: data at rest, data in use, and data in motion. This way, your data is safe at all times.
Do you want to know more about our secure solutions at Lizard Global? Or do you have questions about our security systems you’d like to ask our experts? Get in touch with us, and we gladly tell you all you need to know about the protection of your personal data.

FAQs

What are the key aspects when developing a secure application at Lizard Global?
How do we build a secure application at Lizard Global?
What justifies the need for secure application development?







