authentication
customer identity and access management
+ 4 more ...
What is CIAM and Why Does It Matter?
03 Jun 2021
by Lotte, Digital Content Specialist
03 Jun 2021
by Lotte, Digital Content Specialist
authentication
customer identity and access management
CIAM
identification
identity management
accessibility
What is CIAM and Why Does It Matter?
Table of contents
Contact us
We will get back to you in the next 48 hours.

Tokens are used to authenticate and authorize users on the world wide web and make sure that only validated identities can access or transfer specific information.
CIAM stands for Customer Identity and Access Management and can be defined as the collection of processes, products, services and policies that are implemented to manage user identities and regulate user access. Organizations making use of CIAM usually do this to form a unique and valuable combination of security and convenience which directly impacts the overall customer experience. This blog dives deeper into customer identity and access management and its benefits for both organizations and customers.
CIAM for an optimized customer experience.
As the name suggests, CIAM is all about your customers - specifically their data and the safety thereof. In order to provide the best possible customer experience, it’s essential that you have clear insights into what your customers like and don’t like. With this information, you can make sure the right service or product is being recommended to the right customer. This saves your customers time and effort while increasing your profit at the same time. It’s a win-win! However, the collection of personal user information goes hand-in-hand with data security, which also forms an integral part of CIAM. User data can be a great asset to increase your profits unless it falls into the wrong hands. CIAM is all about transparency and providing clear insights into what data is being collected.
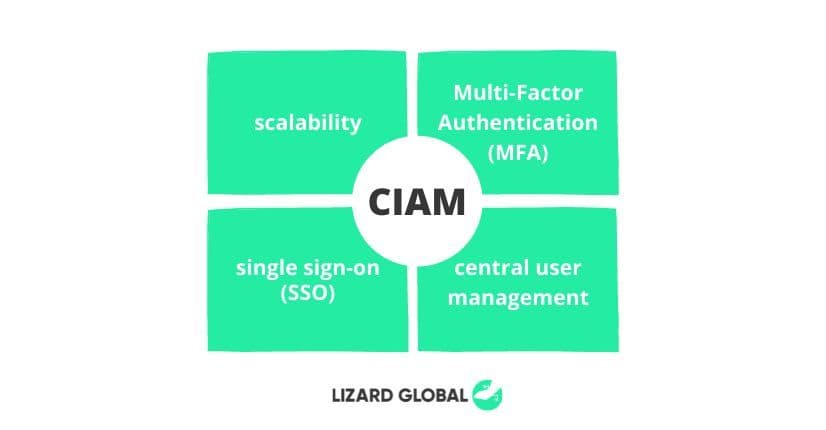
Digital practices of CIAM have been evolving over the years in order to keep up with the often conflicting demand between privacy, security, control, and the desire to get to better know your customers and their preferences. In a very competitive online sphere of countless tools and services, the best way to attract and retain customers is by providing an immaculate customer experience catered to your customer’s interests and needs. One way to do this is by offering a convenient, secure and personalized experience, in which the customer can smoothly navigate through your platform. Generally, the most powerful CIAM consists of four core features that provide optimal value for organizations:
1. Scalability
Because CIAM collects and analyses user data in order to provide personalized customer experiences, it has to obtain, store and scale up to millions or even billions of individual users and their data. Because of that, scalability is a unique core element of CIAM that often relies upon third-party cloud service providers. These third-party services are great tools to store your personal data to save space on actual hardware and to prevent an overload on servers. However, when using these third-party platforms, it’s essential to make sure these parties are GDPR compliant and therefore trustworthy and secure by law.
2. Single sign-on
Single Sign-On, or SSO, allows users to instantly and securely be logged into multiple applications with a single account. By logging into one application, related applications automatically come along. Think of, for example, Google G Suite, which allows users to log into Gmail and automatically logs them into Google Drive, YouTube and other Google platforms. Third-party applications and/or platforms such as Asana or ClickUp also provide the option to log in with your Google account, even though these platforms aren’t directly owned by Google. By allowing users to use their social logins on multiple platforms at the same time greatly simplifies the registration process and therefore optimizes the overall customer experience, which can eventually lead to increased conversions and customer retention.
3. Multi-factor authentication
The most secure CIAM solution consists of MFA and so-called brute force protection. MFA stands for multi-factor authentication, which means that users need to provide at least two different elements to prove their identity. This can be, for example, a password and a secret code sent to your phone. MFA protects its users by providing a secondary layer of protection in the form of, for example, a personal code sent to your phone.
The term “brute force protection” refers to the limitation of login attempts by potential attackers by implementing Strong Password Requirements, such as the requirement of a minimum amount of numbers, capital letters and signs. This makes it almost impossible for hackers to guess your password. Some hackers make use of brute force attacks that consist of an exhaustive attempt to guess login information by trial and error. Brute force protection can make sure that the attacker can’t endlessly try out passwords by temporarily blocking login attempts. Just like your bank card, which is usually limited with three pin code attempts, your password can also be guessed a limited number of times before it gets temporarily blocked.
4. Centralized user management
One of CIAM’s strengths involves the collection and analysis of user data. Insights into user data can form a major advantage, such as being able to offer personalized experiences based on collected data which can greatly improve the customer experience. While collecting this one thing, actually using it is a second. In order to use data in an optimized way, it needs to be organized, easily accessible and accurate at all times. Centralized user management in the form of data dashboards with structured data collections and visualizations is a good way to stay in control of your customers’ data in a controlled manner. It’s not only efficient for analytics, but it also helps companies meet reporting requirements made by data privacy laws.
Identity management & access control
Identity management has everything to do with the identification and authentication of users online. This way, organizations can make sure that access to their systems and potential sensitive documents are securely controlled. Only users with a validated identity are granted access to these documents. So, CIAM is used to collect user data to provide an optimized customer experience, while also protecting organizations from intruders accessing their personal information and documents by validating who has the rights to view this data.
The more data that’s being collected and stored online, the higher the risk is that the data will become a target of people with bad intentions. By the means of so-called “broken authentication hacks”, hackers can steal user credentials. There are currently billions of stolen passwords and other sensitive data being passed around on the dark web? That’s reason enough to consider a solid protection strategy. Curious if your private data is known to be part of a data breach? Sites like haveibeenpwned.com give you an insight into potential data leaks of your personal information on the internet.
So, how does CIAM fit in the picture of user data protection? Generally, a steady CIAM solution possesses the right security features to protect your organization and customers against breaches, hacks and fraud.
So, why CIAM?
As mentioned above, CIAM can have a major impact on the overall experience and retention of your customers, while also providing your business with valuable insights into their behaviour and needs. Next to that, it allows your organization to control and manage access to services and potentially sensitive company data. Want to know more about CIAM, or are you interested in how Lizard Global handles the security of user data? Get in touch with our specialists, and we gladly tell you more.
Are you looking for a digital partner for the development of your web- or mobile application? Get in touch with us via WhatsApp, email, our contact form, or give us a call.

Tokens are used to authenticate and authorize users on the world wide web and make sure that only validated identities can access or transfer specific information.
CIAM stands for Customer Identity and Access Management and can be defined as the collection of processes, products, services and policies that are implemented to manage user identities and regulate user access. Organizations making use of CIAM usually do this to form a unique and valuable combination of security and convenience which directly impacts the overall customer experience. This blog dives deeper into customer identity and access management and its benefits for both organizations and customers.
CIAM for an optimized customer experience.
As the name suggests, CIAM is all about your customers - specifically their data and the safety thereof. In order to provide the best possible customer experience, it’s essential that you have clear insights into what your customers like and don’t like. With this information, you can make sure the right service or product is being recommended to the right customer. This saves your customers time and effort while increasing your profit at the same time. It’s a win-win! However, the collection of personal user information goes hand-in-hand with data security, which also forms an integral part of CIAM. User data can be a great asset to increase your profits unless it falls into the wrong hands. CIAM is all about transparency and providing clear insights into what data is being collected.
Digital practices of CIAM have been evolving over the years in order to keep up with the often conflicting demand between privacy, security, control, and the desire to get to better know your customers and their preferences. In a very competitive online sphere of countless tools and services, the best way to attract and retain customers is by providing an immaculate customer experience catered to your customer’s interests and needs. One way to do this is by offering a convenient, secure and personalized experience, in which the customer can smoothly navigate through your platform. Generally, the most powerful CIAM consists of four core features that provide optimal value for organizations:
1. Scalability
Because CIAM collects and analyses user data in order to provide personalized customer experiences, it has to obtain, store and scale up to millions or even billions of individual users and their data. Because of that, scalability is a unique core element of CIAM that often relies upon third-party cloud service providers. These third-party services are great tools to store your personal data to save space on actual hardware and to prevent an overload on servers. However, when using these third-party platforms, it’s essential to make sure these parties are GDPR compliant and therefore trustworthy and secure by law.
2. Single sign-on
Single Sign-On, or SSO, allows users to instantly and securely be logged into multiple applications with a single account. By logging into one application, related applications automatically come along. Think of, for example, Google G Suite, which allows users to log into Gmail and automatically logs them into Google Drive, YouTube and other Google platforms. Third-party applications and/or platforms such as Asana or ClickUp also provide the option to log in with your Google account, even though these platforms aren’t directly owned by Google. By allowing users to use their social logins on multiple platforms at the same time greatly simplifies the registration process and therefore optimizes the overall customer experience, which can eventually lead to increased conversions and customer retention.
3. Multi-factor authentication
The most secure CIAM solution consists of MFA and so-called brute force protection. MFA stands for multi-factor authentication, which means that users need to provide at least two different elements to prove their identity. This can be, for example, a password and a secret code sent to your phone. MFA protects its users by providing a secondary layer of protection in the form of, for example, a personal code sent to your phone.
The term “brute force protection” refers to the limitation of login attempts by potential attackers by implementing Strong Password Requirements, such as the requirement of a minimum amount of numbers, capital letters and signs. This makes it almost impossible for hackers to guess your password. Some hackers make use of brute force attacks that consist of an exhaustive attempt to guess login information by trial and error. Brute force protection can make sure that the attacker can’t endlessly try out passwords by temporarily blocking login attempts. Just like your bank card, which is usually limited with three pin code attempts, your password can also be guessed a limited number of times before it gets temporarily blocked.
4. Centralized user management
One of CIAM’s strengths involves the collection and analysis of user data. Insights into user data can form a major advantage, such as being able to offer personalized experiences based on collected data which can greatly improve the customer experience. While collecting this one thing, actually using it is a second. In order to use data in an optimized way, it needs to be organized, easily accessible and accurate at all times. Centralized user management in the form of data dashboards with structured data collections and visualizations is a good way to stay in control of your customers’ data in a controlled manner. It’s not only efficient for analytics, but it also helps companies meet reporting requirements made by data privacy laws.

Identity management & access control
Identity management has everything to do with the identification and authentication of users online. This way, organizations can make sure that access to their systems and potential sensitive documents are securely controlled. Only users with a validated identity are granted access to these documents. So, CIAM is used to collect user data to provide an optimized customer experience, while also protecting organizations from intruders accessing their personal information and documents by validating who has the rights to view this data.
The more data that’s being collected and stored online, the higher the risk is that the data will become a target of people with bad intentions. By the means of so-called “broken authentication hacks”, hackers can steal user credentials. There are currently billions of stolen passwords and other sensitive data being passed around on the dark web? That’s reason enough to consider a solid protection strategy. Curious if your private data is known to be part of a data breach? Sites like haveibeenpwned.com give you an insight into potential data leaks of your personal information on the internet.
So, how does CIAM fit in the picture of user data protection? Generally, a steady CIAM solution possesses the right security features to protect your organization and customers against breaches, hacks and fraud.
So, why CIAM?
As mentioned above, CIAM can have a major impact on the overall experience and retention of your customers, while also providing your business with valuable insights into their behaviour and needs. Next to that, it allows your organization to control and manage access to services and potentially sensitive company data. Want to know more about CIAM, or are you interested in how Lizard Global handles the security of user data? Get in touch with our specialists, and we gladly tell you more.
Are you looking for a digital partner for the development of your web- or mobile application? Get in touch with us via WhatsApp, email, our contact form, or give us a call.
FAQs

What is CIAM?
Why is CIAM important?
What is the difference between access management and identity management?
What is MFA?
What is brute force protection?







